JADX + AI Copilots: Smarter Droid Analysis
Hack smarter, crack deeper: Jadx + AI copilots redefine Android application (APK) security analysis like a goddess.
Introduction
Jadx has always been a go-to for decompiling and analyzing APKs—but with AI copilots like Claude, Ollama, Cherry Studio, and LM Studio running in HTTP stream mode, the game has changed. APK cracking becomes smoother, Droid analysis smarter, and application security sharper. AI copilots enhance navigation, code understanding, and vulnerability hunting, turning complex reverse engineering into an intuitive process. Together, Jadx and AI copilots redefine how we secure mobile applications in a world where speed and intelligence matter most.
Prerequisites
Before starting pentesting with Jadx + AI copilots, ensure you have:
- Jadx-GUI installed
- Emulator or Android device for testing
- An APK you control (test target)
- Claude Desktop (see Claude Desktop Debian Build)
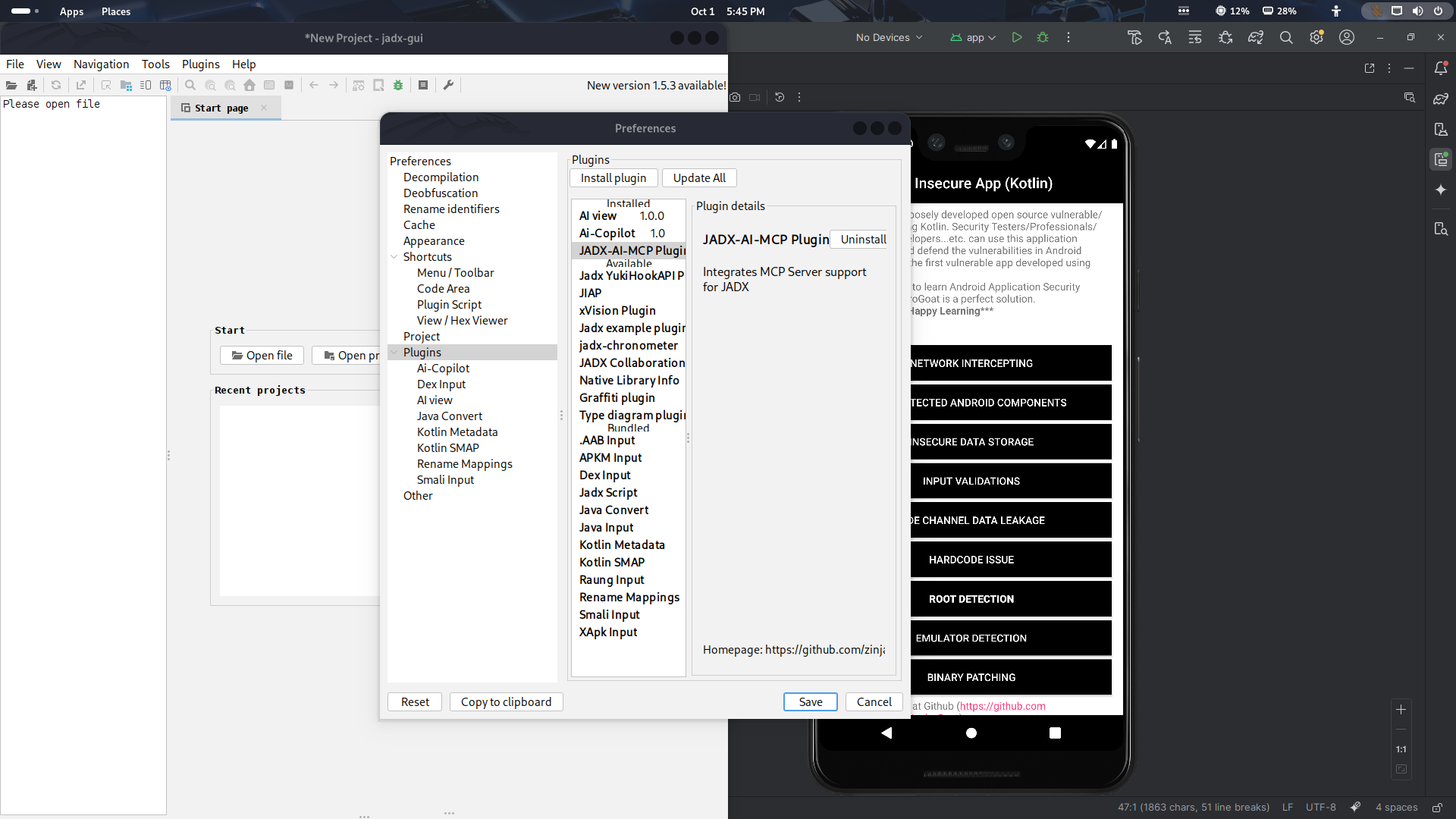
- jadx-ai-mcp plugin installed via:
1
./jadx plugins --install "github:zinja-coder:jadx-ai-mcp"
Step 1: Install Claude Desktop (Debian/Kali)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
cd ~
# Clone the Debian package repo
git clone https://github.com/aaddrick/claude-desktop-debian.git
# Install dependencies
sudo apt update && sudo apt install -y wget git unzip python3 python3-venv
# Build and install Claude Desktop
cd claude-desktop-debian
./install.sh
# Launch
claude-desktop
Step 2: Install uv (for MCP servers) and jadx-mcp-server
1
2
3
4
5
6
7
8
9
10
11
12
13
#install uv
curl -LsSf https://astral.sh/uv/install.sh | sh
source ~/.bashrc
uv --version
# Clone jadx mcp Server
cd ~
git clone https://github.com/zinja-coder/jadx-mcp-server.git
#Confirm Path to uv
which uv
Step 3: Configure Claude Desktop with MCP
1
nano ~/.config/Claude/claude_desktop_config.json
Paste the following contents into the config file
1
2
3
4
5
6
7
8
9
10
11
12
13
{
"mcpServers": {
"jadx-mcp-server": {
"command": "/home/<YOUR_USERNAME>/.local/bin/uv",
"args": [
"--directory",
"/home/<YOUR_USERNAME>/jadx-mcp-server/",
"run",
"jadx_mcp_server.py"
]
}
}
}
You now have Claude Desktop + Jadx MCP fully integrated in Kali, ready for AI-powered APK pentesting.
Confirm in the plugins section of your Jadx-gui
AI-Driven Droid Analysis with Jadx + Claude
Now, let’s dive into understanding code with the combined power of Jadx and Claude.
Jadx + Claude Capabilities
Pentesting with AI: Claude + Jadx for Android Security
Jadx + Claude — Explain Code Sections
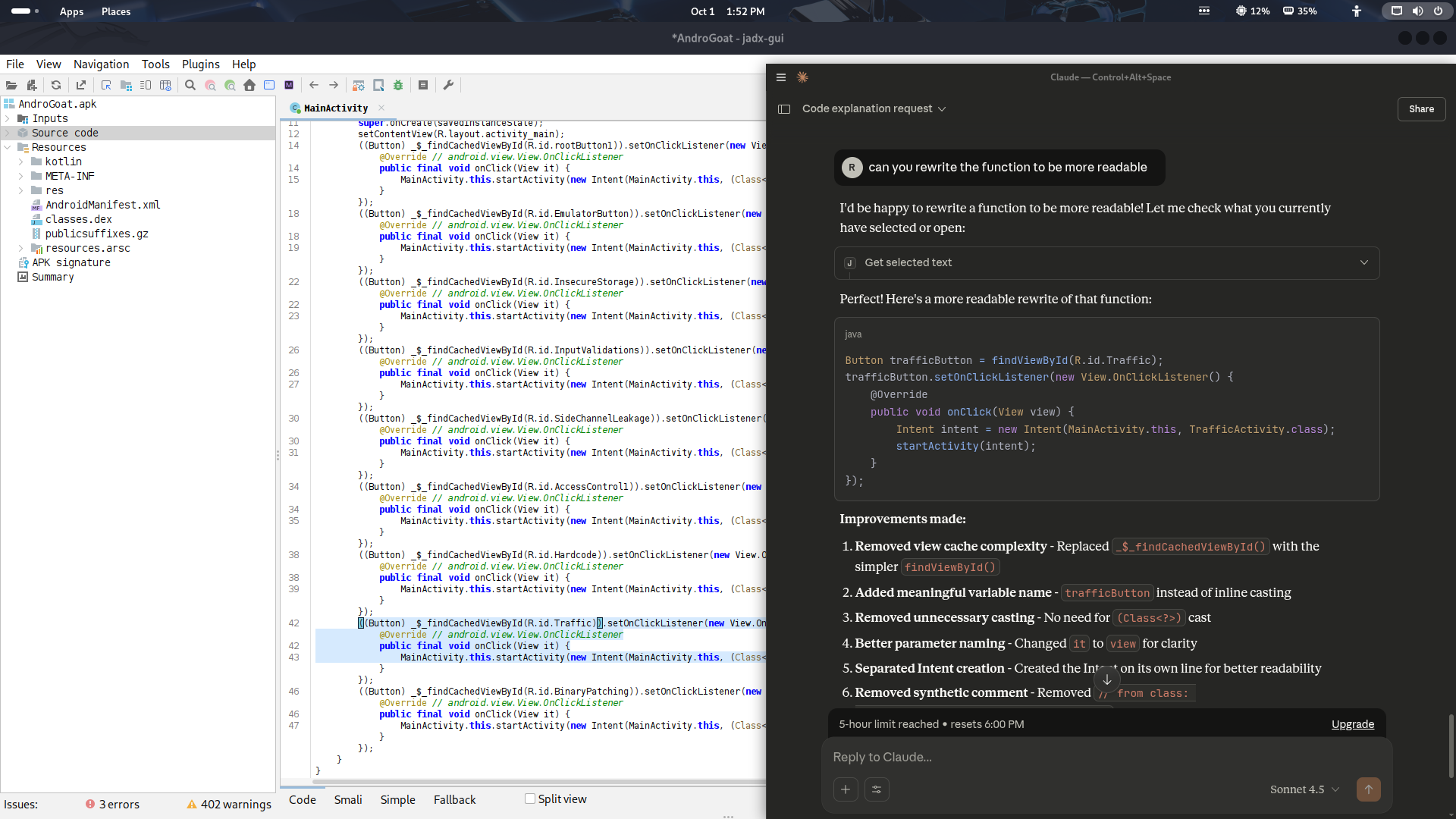
Rewrite code for noobies like I.
Understanding Code as a noobie
Indentify the Attack Vectors
First it was to determine the attack vectors via our android manifest file.We find that there some exported activities.
Identifying the Attack Vectors using Claude
Services: Enumeration & Abuse (Jadx + Claude)
Decompile service code with Jadx to inspect exposed APIs and IPC; use Claude to highlight unsafe entry points and attack vectors.
Enumerating and abusing services using AI
Deep Link Analysis & Exploitation (Jadx + Claude)
Catalog deep-link declarations with Jadx and employ Claude to identify parsing flaws, open redirects, and exploit hypotheses.
Deep Link Analsis using AI
Conclusion
Jadx + AI copilots have already shown how much smarter — and faster — Droid analysis can be. In this post we walked through static enumeration, deep-link and service review, and how Claude helps explain tricky code paths and surface likely attack vectors. Next, we’ll extend the workflow to integrate other copilots (Ollama, Cherry Studio, LM Studio and more), broaden HTTP stream-mode tooling, and demonstrate cross-tool playbooks for real-world pentests.
AI isn’t a silver bullet, but its ability to summarize, prioritize, and generate repeatable test cases makes it an indispensable force multiplier for application security.
🙏 Special thanks to zinja-coder’s jadx-ai-mcp project
Remember friends: good prompts, good output — garbage in, garbage out.
⚠️ For educational use only — apply Jadx + AI analysis responsibly on apps you own or have permission to test.
More coming soon on dynamic Analysis using AI